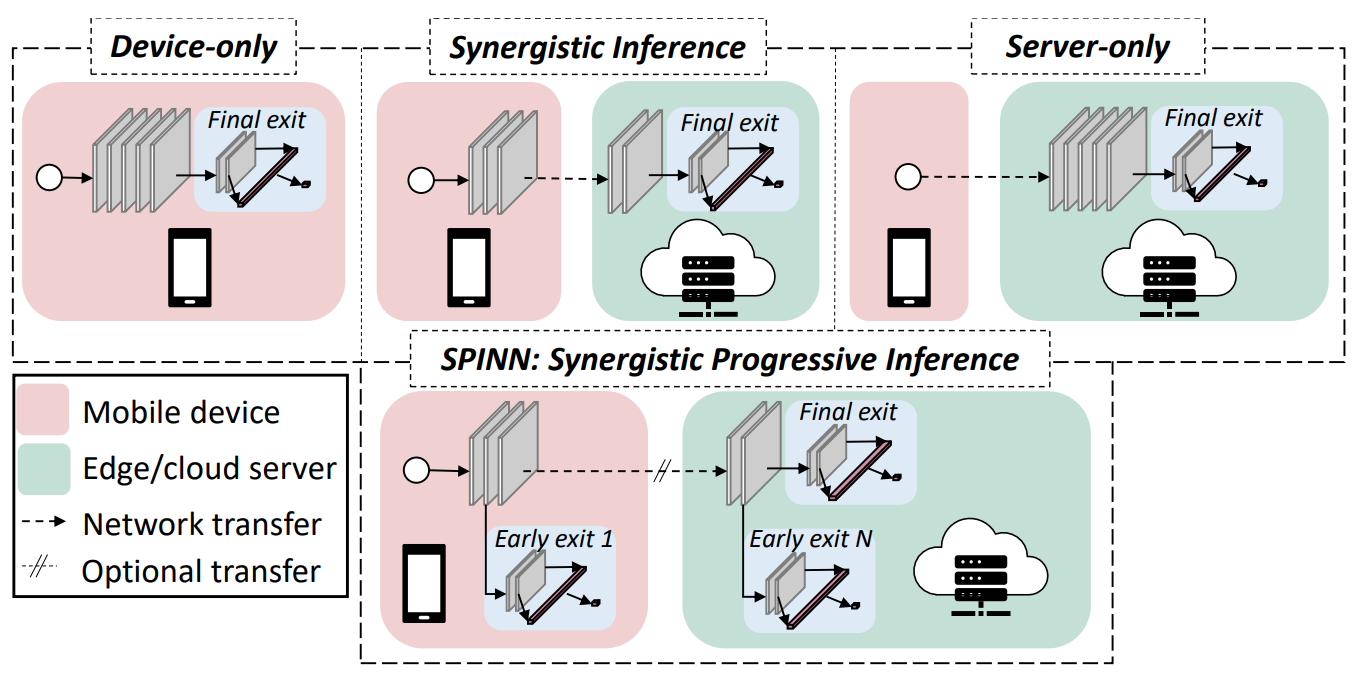
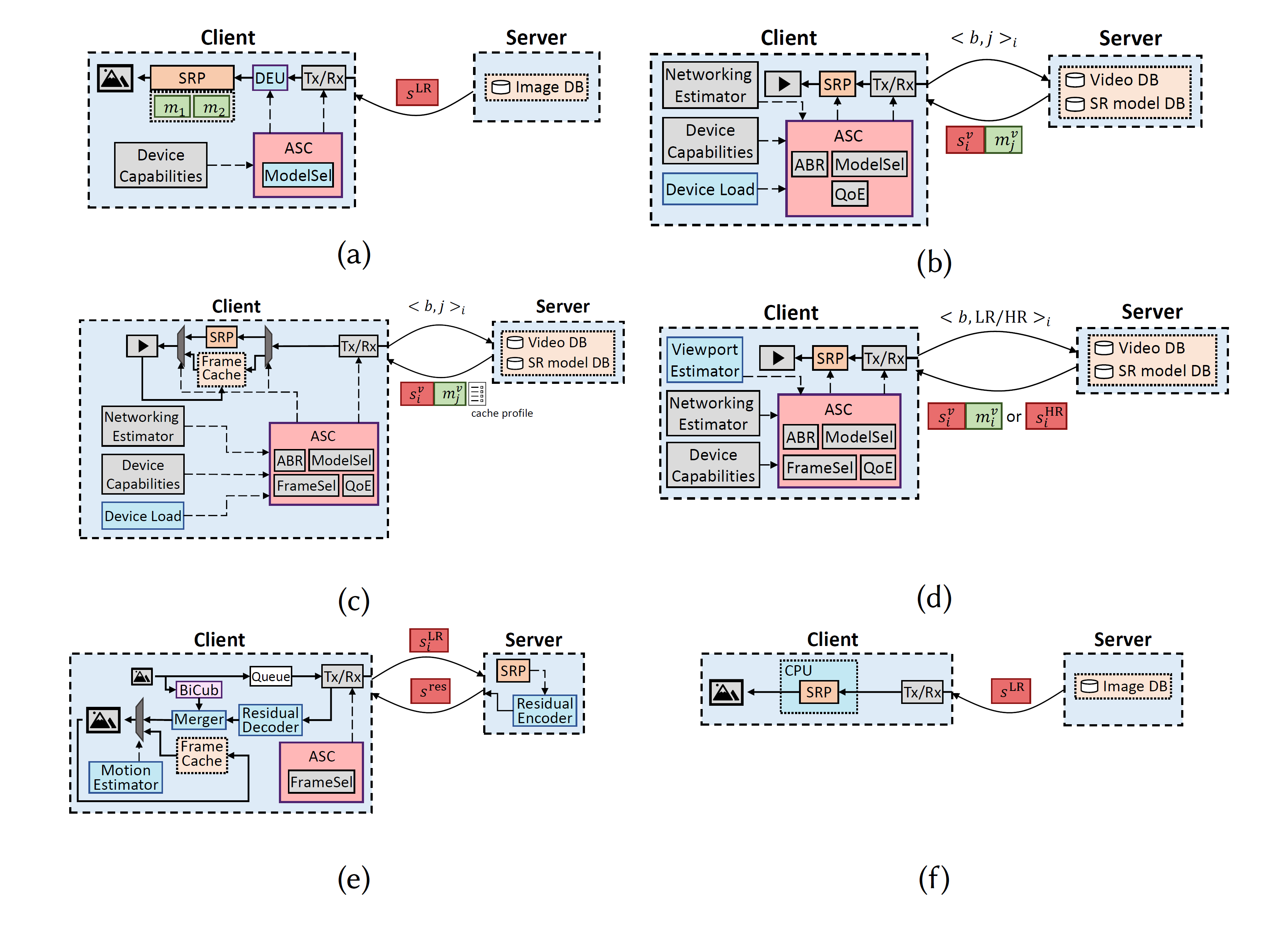
PDF) Artificial neural networks and iterative linear algebra methods | K.G. MARGARITIS - Academia.edu
PDF) Adoption of Biometric Authentication Systems: Implications for Research and Practice in the Deployment of End-User Security Systems

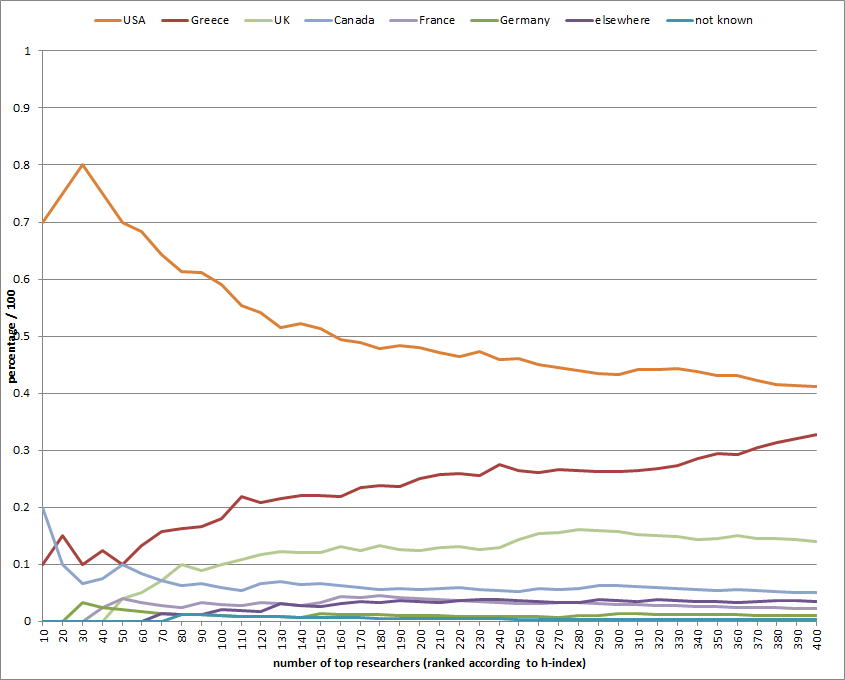
PDF) Biometrics and e-Identity (e-Passport) in the European Union: End-User Perspectives on the Adoption of a Controversial Innovation